
Mandated by the FBI, compliance to the CJIS Security Policy is non-negotiable for law enforcement agencies and vendors that handle Criminal Justice Information (CJI). So, the question “why is CJIS compliance mandatory?”naturally comes up quite often.
The short answer is data security. As CJI databases contain highly sensitive information, the FBI places strict requirements for its protection. Mandatory CJIS compliance police software guarantees that sensitive data are secured throughout its entire lifecycle.
Regardless of whether you’re accessing NCIC, NLETS, state systems, or local repositories, agencies and vendors alike need to be CJIS-compliant. This is to ensure officer safety, public safety, and smooth agency operations, as well as avoid legal liability. Failure to do so leads to an immediate loss of access to CJI databases.
This article clarifies the legal foundation of the mandatory CJIS standards for police work, its benefits, and consequences of non-compliance. It also breaks down the CJIS requirements for law enforcement software, so that you can confidently choose one that genuinely safeguards your agency.

The Federal Mandate: Legal Foundation of CJIS Compliance Requirements
State regulations or preferences of the agency do not determine the understanding of CJIS requirements for law enforcement. The federal statute directly influences that understanding.
The law under 28 U.S.C. § 534 gives the FBI the authority to regulate the National Crime Information Center (NCIC) and all databases of national criminals explicitly. This legislation has supported the police CJIS standards as a legal obligation, not as a practice, not as a suggestion, but as federal law.
The CJIS Security Policy of the FBI’s Criminal Justice Information Services (CJIS) Division is the document that dictates security, audit, and operational requirements set by the agency. The policy is reviewed regularly for changes in technology and threats. All the agencies and vendors are required to do the same.
The Multi-Level Enforcement Chain
The trajectory of the mandate from the federal level down to the local level is as follows:
- Federal level: The FBI formulates the CJIS Security Policy
- State level: The CJIS Systems Officer (CSO) makes sure that the state follows the rules
- Agency level: Every department is responsible for reaching and maintaining compliance
- Vendor level: Any software vendor granted access to CJI must be CJIS compliant
The Security Addendum is the legal document that seals the deal for all parties involved. All agencies that have access to FBI databases and vendors providing software have to sign this legal contract. It is not a choice; it is as compulsory as a business contract.
State and local agencies do not have an option to refuse participation. The Compact Council, which represents state leaders, is the one that makes sure compliance is met all over the country.
If your agency is not compliant, your state Chief Security Officer (CSO) has the authority to disconnect your agency’s access to the database. And it will happen.
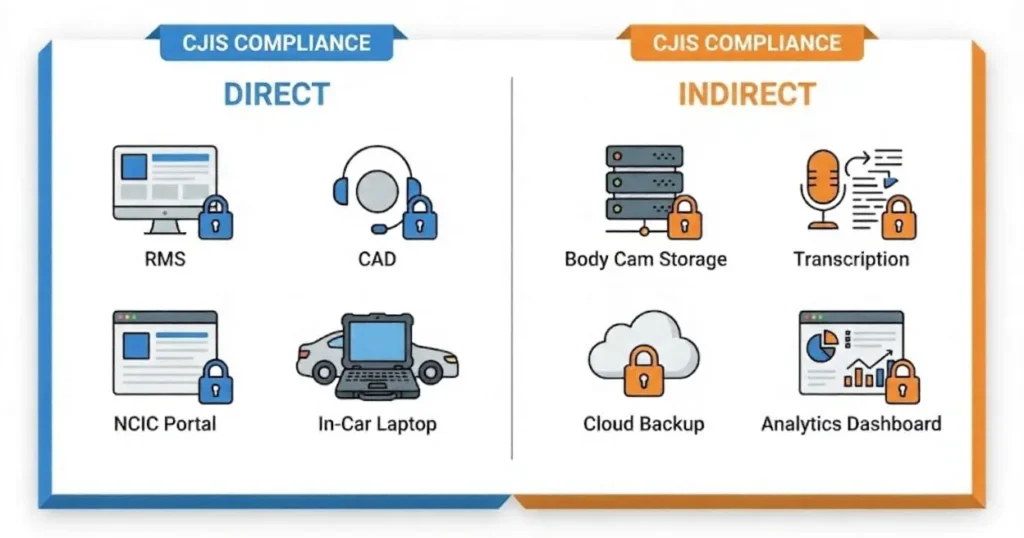
What Makes Police Software Subject to CJIS Compliance?
In considering CJIS requirements, law enforcement agencies and vendors need to evaluate their police software. According to the FBI’s Criminal Justice Information Services (CJIS) Security Policy, any system that has access to, stores, processes, or transmits Criminal Justice Information (CJI) needs to be compliant.
Modern policing software is affected by this trigger almost entirely. If there is any doubt, consider it to be compliance, and check it with your state CJIS Security Officer (CSO) immediately.
Direct access systems
Real-time operations require direct access systems to manage CJI, and such systems are subjected to rigorous controls like encryption and audit logs:
- RMS (Records Management Systems): RMS serves as the repository for the police to save arrest records and incident reports that have CJI in their content.
- CAD (Computer-Aided Dispatch): CAD processing systems transmit CJI during emergencies along with the suspect detail calls.
- Database access portals (NCIC, NLETS queries): Officers get the information needed for warrants and stolen property checks by querying NCIC through authorized systems as per 28 U.S.C. § 534.
- Mobile data terminals and in-vehicle systems: Patrol cars use laptops or tablets connected to the national databases to access CJI.
- Evidence management systems: The CJI embedded in photos, videos, and documents is managed by these systems.
Indirect access systems
Indirect access systems interact with CJI secondarily but still require compliance:
- Body camera footage storage: Videos that contain identifiable CJI need to be stored securely either in the cloud or on-premises.
- Transcription services: AI tools are used to process body cam audio that contains suspect statements or victim data.
- Cloud backup systems: All backups of files that bear CJI must comply with CJIS encryption standards.
- Case management platforms: Account for investigations with CJI references in different departments.
- Analytics and reporting tools: Collect statistics related to crime that come from CJI sources.
All vendors’ responsibilities are non-negotiable; whenever their software interacts with CJI, they shall meet the mandatory CJIS standards for police.
The “direct vs. indirect” differentiation affects implementation (e.g., direct needs FIPS 140-2 validation), but both still require the same level of protection.
In case of cloud services or doubts, take compliance for granted and get in touch with your state CJIS Security Officer (CSO) for a clear CJIS compliance manual for police software.
This ensures that strong law enforcement software CJIS requirements are maintained across the country.

Critical Consequences of Non-Compliance with Mandatory CJIS Standards
Non-compliance with mandatory CJIS standards for police leads to halting of law enforcement operations and puts agencies at a severe risk. Agencies must give top priority to CJIS compliance in order to protect criminal justice information (CJI) and maintain the integrity of operations.
Understand why CJIS compliance is mandatory in the first place to avoid these disastrous outcomes affecting not only officers but also agencies and communities.
Immediate Operational Consequences
Agencies that do not comply with regulations will immediately have their access to the database terminated, which will significantly affect daily police work. During critical confrontations, officers are deprived of crucial means, and investigations are halted entirely.
- Instant database access termination: Loss of NCIC, NLETS, and state criminal databases, resulting in agencies being cut off from essential intelligence.
- Officer safety risks: There will be no warrant checks, ID verifications, or stolen property checks during traffic stops, thus posing a threat to lives.
- Stalled Investigation: Active cases will be stalled due to a lack of access to criminal histories or fingerprint databases.
- Dispatch disruption: During emergencies, 911 operators are unable to perform queries of databases, thus prolonging the responses.
- Inter-agency cooperation breakdown: Other agencies will not share CJI with non-compliant partners.
- Evidence compromised: If the evidence chains involve non-compliant systems, the courts will dismiss the cases.
Legal and Regulatory Consequences
Enforcement by both federal and state authorities occurs when police violate the mandatory CJIS standards. The individuals who are in charge are held personally liable, hence the stakes are raised.
- Federal Penalties: Violations of 28 U.S.C. § 534 mean the Department of Justice investigates and fines.
- Penalties from states: Each state has its own penalties, which may include temporarily closing the police department.
- Civil liability: People whose CJI was wrongly accessed or disclosed can sue.
- Criminal liability: Intentional disregard to comply results in charging IT personnel, chiefs, and administrators.
- Contract Violations: Lose federal loans and state financing that are subject to compliance.
- Impacts on vendors: The exit of software manufacturers from the police market to the detriment of law enforcement agencies’ options.
Financial Consequences
Remediation costs are a significant burden on agencies with already stretched budgets. One of the consequences of non-compliance is that agencies must pay a high price for delays in the process of obtaining CJIS certification.
- Remediation costs: The cost of emergency measures is often a lot more than the cost of proactive implementation.
- Breach notification expenses: Data incidents from non-compliance trigger mandatory reporting fees.
- Legal defense costs: High attorney bills cut through defending against lawsuits and audits.
- Lost productivity: The operations are stopped during the fixing period, causing officers and staff to be idle.
- Insurance impacts: Premiums go up drastically, or the insurance is cut off because of non-compliance.
- Grant ineligibility: Federal and state funding that is tied to CJIS adherence gets missed.
Reputational and Trust Consequences
Public exposure destroys confidence in the agency’s skill and competence. The leaders of the agency take the blame personally.
- Public trust erosion: The community has significant questions about the agency’s ability to protect data.
- Media scrutiny: The breaches maintain the headlines and damage the agency’s credibility in the long run.
- Recruitment/retention effects: The best workforce is not attracted to or is leaving the agencies that are not complying with the required standards.
- Inter-agency relationships damaged: Data-sharing with neighbors is cut off.
- Political pressure: The elected are asking the agency for accountability concerning the failures.
- Career consequences: IT directors, managers, and administrators will risk their jobs.
Real-World Risk Example
- During a standard traffic stop, an officer without NCIC access due to non-compliance overlooked an active warrant, which resulted in a shootout, and the officer and suspect were injured.
- The dispatch did not confirm the 911 caller’s vehicle status, which caused a delay in backup and opened up the possibility of a chase.
- The investigators’ progress was hindered as they had to throw away evidence that the compromised system had provided, which delayed a multi-agency drug probe.
Get compliant software now to protect your agency from these cascading failures. CJIS compliance importance compels instant action for seamless operations and officer safety.

Essential Benefits of CJIS Compliance for Police Operations
CJIS compliance allows police departments to realize full operational efficiency without interruptions, along with greater safety for their officers, as it gives them access to the essential national databases like NCIC in their entirety.
The agencies maintain seamless connections to NLETS and the state computer systems, which means that the officers can get the vital information right away during the critical moments of confrontation.
The enforcement of the mandatory CJIS standards for police transforms legal compliance into a strategic investment that raises law enforcement capabilities even more than just the avoidance of penalties.
Operational Benefits
The CJIS compliance benefits have a significant impact on the daily operations across police functions. The departments will experience the following:
- Uninterrupted database access: The officers get connected to NCIC, NLETS, and the state systems reliably with no interruptions, enabling them to do their mission-critical queries continuously.
- Officer Safety Enhancement: The real-time checks of warrants, the provision of gang affiliation data, and the issuing of officer safety bulletins are ways of providing immediate intelligence to protect those personnel who are in the field.
- Faster investigations: Detectives are able to get access to criminal histories, fingerprint matches, and case linkages instantly, enabling them to speed up case resolution from days to minutes.
- Improved dispatch effectiveness: The 911 operators can get critical details very quickly from their computer, which helps to improve accuracy and reduce interference caused by pressure.
- Mobile field capabilities: The patrol officers are able to query the databases while still in their vehicles or on their devices, supporting proactive policing without the need to go back to the headquarters.
- Collaboration of inter-agency: The secure data sharing with partners from federal, state, and local sectors helps the smooth running of joint operations and multi-jurisdictional pursuits.
Security and Risk Management Benefits
Resilient CJIS standards strengthen the preventive barriers against contemporary threats. Authorities are executing the following:
- Data breach prevention: Unauthorized external access to sensitive CJI is not allowed, as there are security measures in place to protect it.
- Insider threat mitigation: Criminal justice information is safeguarded against internal misuse due to the monitoring trails and access controls determined by roles.
- Cybersecurity posture: CJIS is in complete alignment with NIST frameworks, providing the law enforcement industry with comprehensive protection that is specially created for its needs.
- Incident response readiness: Teams are provided with plans that are suggested by the authorities to efficiently detect, contain, and recover from breaches.
- Compliance documentation: Agencies are provided with pre-audited records that help them avoid liability during federal reviews.
Financial and Administrative Benefits
Compliance results in clear and quantifiable cost savings and improvements in the process. Significant benefits are as follows:
- Federal grant eligibility: A lot of the funding programs demand CJIS compliance, which means access to significant resources for training and proficiency development.
- Reduced liability exposure: Confirmed adherence leads to the minimization of lawsuits, fines, and the costs of repairing the situation caused by data incidents.
- Vendor accountability: The Security Addendum places the vendor’s responsibility, and the software provider takes over the risks associated with a breach.
- Streamlined audits: Well-organized records make the verification of compliance an easy routine rather than a disruptive ordeal.
- Insurance advantages: The implementation costs are compensated as the insurers tend to cut down the cyber premiums for those agencies that are CJIS-compliant.
Public Trust and Accountability Benefits
Adherence to CJIS requirements significantly enhances the organization’s reputation among stakeholders. The departments create:
- Community confidence: The agency’s operations become more trustworthy to the public because of the secure way of handling personal data.
- Transparency and accountability: The extensive audit trails provide evidence for the proper use of CJI, effectively meeting the requirements for oversight.
- Professional reputation: The compliance indicates the commitment to the very best data security practices.
- Recruitment advantage: The modern secure systems attract the best personnel who prefer the latest tools.
Long-Term Strategic Benefits
Agencies that are thinking forward take the necessary steps to grow. Compliance provides:
- Infrastructure for the future: AI analytics and predictive policing tools are founded on these supportable layers.
- Interoperability: Technology will be adopted through the use of common standards, and no major renovation would be necessary.
- Scalability: As agencies grow and data volume increases, the systems will be expanded without any hassle.
The CJIS compliance benefits are not just limited to the regulatory requirements; police departments that prioritize those mandatory CJIS standards for police will be in a better position regarding efficiency, security, and sustainability.
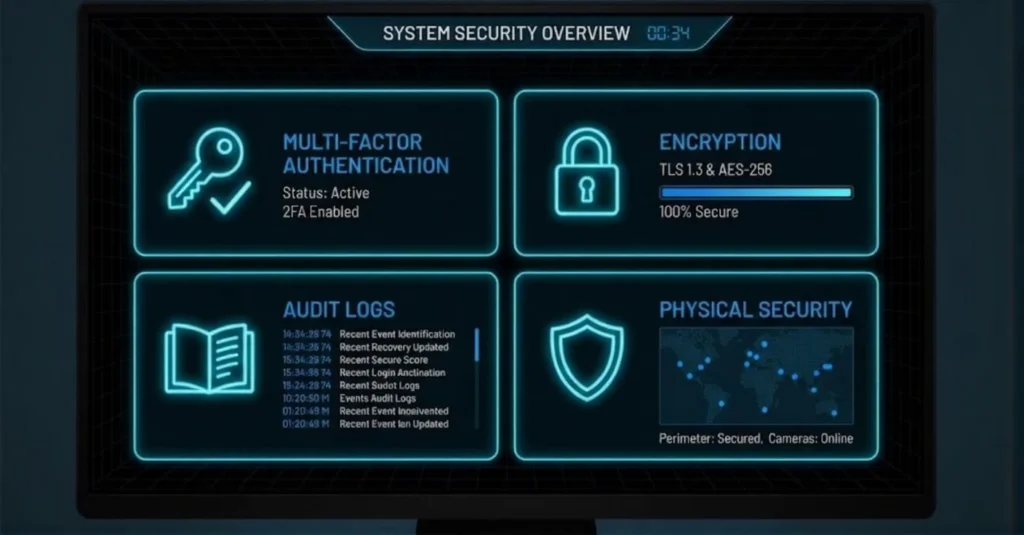
Core CJIS Requirements Every Police Software Solution Must Meet
To comply with strict CJIS standards, law enforcement agencies resort to computer programs that process Criminal Justice Information (CJI). Police software solutions need to fulfill the technical, administrative, and personnel requirements to guarantee security and compliance.
This guide explains the mandatory CJIS standards for law enforcement, which will help the agencies in assessing their existing or future systems against these authoritative standards.
Authentication and Access Control
To secure CJI against unauthorized access, agencies apply rigid access controls, while software vendors make use of such measures to minimize the risks.
- All CJI access requires multi-factor authentication (MFA), which includes something you know (password) along with something you have (token).
- As per CJIS Policy 5.6, strong passwords consist of a minimum of eight characters and require the use of uppercase/lowercase letters, digits, and symbols.
- Role-based access control (RBAC) gives access rights according to the position of the team member and the need-to-know principle.
- Session Management is the process of automatically logging users out due to inactivity after a specified period of time.
- Access reviews are conducted every three months to check if user privileges correspond to their job roles.
Encryption and Data Protection
CJIS imposes strong encryption as a requirement for the protection of CJI during both storage and transmission. Police software solutions put these standards into practice to eliminate the possibility of data breaches.
- Encryption in transit makes use of TLS 1.2 or above for every CJI transmission.
- Encryption for data at rest makes use of AES-256 or similar for CJI data that is kept.
- Encryption key management encompasses secure storage along with periodic rotation processes.
- Encryption for mobile devices has to be full-disk protection for any device that has access to CJI.
- Secure disposal complies with the approved sanitization processes for the media that contains CJI.
Audit and Accountability
Comprehensive logging makes it possible to track all CJI interactions, ensuring accountability. Besides, law enforcement software creates tamper-proof systems for continuous inspection.
- Comprehensive logging keeps track of all actions, modifications, and CJI deletions.
- Tamper-proof audit trails do not allow users to alter or delete logs.
- Log retention lasts at least 1 year, and this period may be prolonged according to state regulations.
- Searchable logs are available to examine and understand access behaviors.
- Frequent log reviews trigger automatic alerts for any irregularities detected.
Physical and Technical Security
Secure environments are there to shield the CJI from both physical and cyber threats. Software solutions, on the other hand, incorporate these controls for dependable operations.
- Secure hosting requires data centers that meet the highest physical security standards.
- Network security uses firewalls and intrusion detection/prevention systems to provide protection.
- Vulnerability management ensures that patching and security updates occur regularly.
- Configuration management assures that system hardening and baseline setups are in place.
- Incident response potential comprises documented, regularly tested procedures.
Personnel Requirements
CJIS compliance is based on personnel evaluation and formal agreements. Agencies keep records of these elements to stay ready for audits.
- To screen the personnel for direct access to CJI, fingerprint-based FBI screening is used for the background checks.
- All CJI user training in security awareness is conducted every year.
- The sanctions policy describes penalties for infractions in a straightforward manner.
- Contractor monitoring guarantees that third-party staff meet the exact requirements.
Administrative Requirements
To comply with CJIS, formal contracts and papers are necessary. Agencies ensure these rules are followed to be ready for audits.
- The Security Addendum is signed by both the FBI and the state CJO.
- Information Exchange Agreements set the rules for the sharing of data between the agencies involved.
- Policy documentation has been written to provide evidence for all 13 areas of the security policy of CJIS that are covered.
- Regular audits that consist of internal evaluations, and the state CJIS does a review every 1-3 years.
Architecture Considerations
Modern designs make law enforcement software CJIS-compliant more efficiently. The different law enforcement agencies select architectures that do not pose risks, while supporting the operations.
- A zero-footprint design takes advantage of browser-based access to reduce the local attack surfaces.
- Cloud and on-premise deployments both come to compliance if done correctly, but their ways of implementation vary.
- API security strengthens the interfaces for the smooth integration of systems.
Understanding CJIS requirements for law enforcement will guarantee that police software complies with the mandatory CJIS standards. This CJIS compliance guide for police software provides agencies with the necessary tools to pick solutions that ensure both security and efficiency in operations.
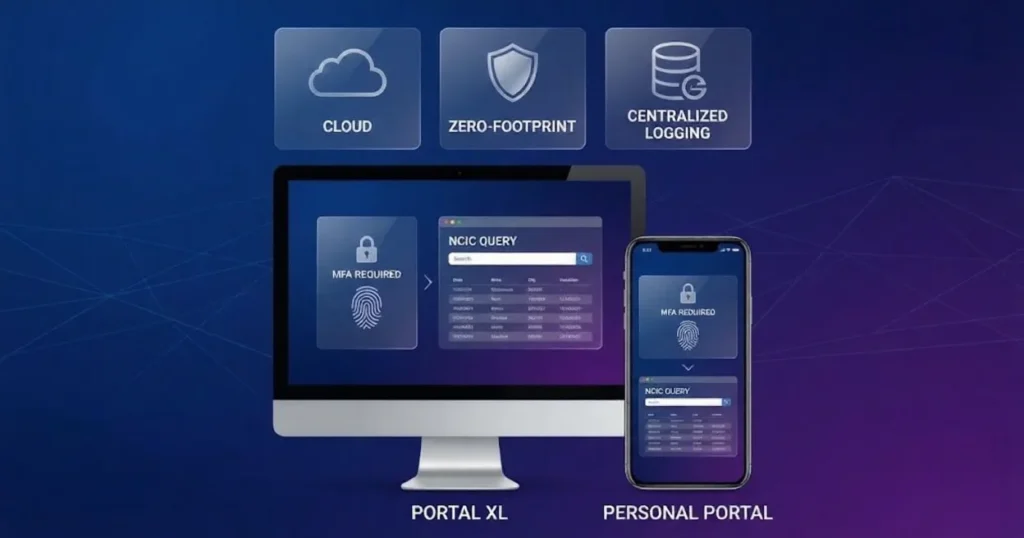
PsPortal: Purpose-Built CJIS-Compliant Infrastructure for Police Database Access
Agencies need to prioritize CJIS-compliant infrastructure for accessing NCIC, NLETS, and state databases at the top of their priorities, as federal mandates set the security standards that must be followed throughout the process.
PsPortal provides this with its foundational layers of Portal XL and Personal Portal, which allow RMS, CAD, and other systems to securely query databases without being in competition against them.
PsPortal has been in the service of law enforcement for over 30 years and embeds compliance from the very beginning, surviving the change of CJIS policies.
Compliance by Design: How PsPortal Meets Mandatory Requirements
PsPortal meets the mandatory CJIS requirements through a system designed for law enforcement processes.
Authentication & Access Control
- The multi-factor authentication ensures that all logins across the products are secure.
- The detailed role-based access controls restrict access according to the roles of officer, supervisor, or administrator.
- The automatic session timeouts are in line with the agency’s policies.
- Native integration with Active Directory or SSO systems is done without any hassle.
Officially, an officer provides their login details along with the token; the system automatically logs out due to inactivity, and the enforcement of access limitations becomes effortless.
Zero-Footprint Architecture
- Browser-based Portal XL does not require any installations at the local level, significantly reducing the surfaces that can be attacked.
- Compliance advantage is that no local storage of CJI data is needed on the staff’s computers, which means that the data is kept in secure data centers.
- Centralized logging makes the audit advantages easier, and scattered local files do not complicate the reviews.
- Updates are instantly deployed from one source to all users.
- BYOD support allows police officers to access the databases through any compliant device.
Compliant agencies receive the benefits without having to replace their hardware completely.
Audit and Accountability
- The use of NCIC and NLETS automatically records every query with the user ID, timestamp, and details.
- The tamper-proof trails are stored securely in a CJIS-compliant system.
- The agencies are instantly prepared for audits by having searchable and exportable logs.
- Alerts signal irregularities such as multiple unsuccessful logins or access during night hours.
Agencies export full logs in a matter of minutes during a CJIS audit and prove accountability automatically without any manual effort.
Encryption and Data Protection
- The data in transit is protected by end-to-end TLS 1.3 encryption, while AES-256 is used for securing data at rest.
- PsPortal keys are managed securely within its infrastructure.
- Zero-footprint guarantees that there is no local CJI storage.
- The Mobile Personal Portal app completely encrypts mobile communications.
An officer in the patrol vehicle queries for warrants, the data is traveling encrypted, logging is capturing everything, and nothing is being stored locally.
Product Suite for Mandatory Access
PsPortal’s tools have a direct impact on the central CJIS requirements.
- Portal XL (Browser-Based): Provides access to NCIC, NLETS, and state through any secure browser. Zero footprint is a guarantee of compliance, and central management takes care of updates and logs.
- Personal Portal (Mobile): Apps for iOS/Android provide full encryption, MFA, and logging for field queries. Lost devices can be securely wiped, and officers can securely run license checks at scenes.
- Testing & Certification Module: Administers NCIC operator certifications, monitors expirations, and restricts access to certified users who meet the imposed requirements.
- Super Administrator (Multi-Agency Management): Supports compliance over a number of agencies, ideal for sheriffs. Unified audits and policy enforcement facilitate the operations between different jurisdictions.
Key Differentiators
PsPortal excels as a purpose-built CJIS compliance technology layer that agencies look for in mandatory access to databases. Law enforcement leaders choose it because of its proven reliability.
- Over 30 years of dedication to law enforcement: Comprehensive understanding of police operations and compliance requirements.
- Compliance expertise: Supports former law enforcement and CJIS experts.
- Continuous compliance updates: PsPortal technology is constantly updated to support the most advanced secure law enforcement software with CJIS compliance
- Audit support: Direct help for preparation and documentation is given.
- Cost efficiency: The use of cloud eliminates the costs of on-premise hardware.
- 24/7 availability: Constant access to the database without any interruptions.
- Seamless interoperability: Works well with existing RMS, CAD, and case management systems.
Agencies validate these differentiators through vendor demos that emphasize the audit trails and zero-footprint access. PsPortal mitigates compliance risks while streamlining the operational process.
Operational Examples
Actual situations demonstrate the implementation of PsPortal’s compliance.
- Dispatch scenario: A 911 dispatcher checks NCIC warrants through the automatic logging of Portal XL access, the data is secured by encryption, and the logs ready for the audit are immediately accessible.
- Field scenario: An officer during a traffic stop makes use of Personal Portal for checks of the driver and vehicle, mobile encryption, and logging to comply with regulations.
- Audit scenario: IT team exports the complete PsPortal logs for state CSO examination, total accountability established, and audit clearance without any delays.
- Multi-Agency scenario: A task force of the county uses Super Administrator for a single monitoring over 12 agencies, which is in accordance with CJIS enforcement throughout the country.
Vendors are assessed by the agencies through the verification of purpose-built, for example, PsPortal CJIS compliance features.
To test the reliability of the compliance, begin with audit log demos and zero-footprint tests.
The PsPortal solution puts police departments in a position where the safety of officers, practical investigations, and hassle-free audits come as benefits.
Selecting CJIS-Compliant Police Software: Critical Evaluation Criteria
Agencies must put police software through a rigorous evaluation process to guarantee compliance with the CJIS standard, since federal mandates require evidence of compliance and not just vendor claims.
With this CJIS compliance guide for police software, those in charge of law enforcement will have the necessary framework to properly evaluate law enforcement software CJIS requirements.
Vendors that demonstrate built-in compliance by means of design and paperwork should be given priority, as this will ensure the protection of officers, the conduct of investigations, and dispatch operations.
After a thorough evaluation, the best CJIS compliance solution for police is the one that not only integrates with existing operations but also reduces operational risks and supports smooth access to critical justice information (CJI) in the long run.
1. Verify Compliance Claims with Documentation
- Insist on receiving a signed CJIS Security Addendum from the FBI, along with the reports of the third-party CJIS compliance audits.
- Personally secure references from agencies in your state with different compliance requirements.
Red flag: Vendors claim to be compliant but do not provide these documents, putting the agencies at risk of failing audits and going through interruptions in their operations.
- Evaluate Architecture for Inherent Compliance
- For easier security management, prefer browser-based and non-installed solutions instead of installed software.
- Verify that CJI storage does not use local devices to minimize the risk of breaches.
- Evaluate centralized update deployment and cloud data center security (including physical protections and redundancy) to keep compliance up to date amid changing threats.
3. Assess Authentication and Access Controls
- Implement multi-factor authentication as a necessity, not as an option, and combine it with elaborate role-based access controls.
- Ensure secure session management and automatic timeouts to prevent unauthorized access.
- Carry out compatibility testing with agency authentication systems to secure operational efficiency.
4. Examine Audit and Logging Capabilities
- Implement a logging system that records the details of every CJI interaction, such as the user, the action performed, the time, and the location.
- Insist on audit trails that cannot be altered and have retention periods that comply with state requirements.
- Ensure that the provision of exportable, searchable reports facilitates CJIS audits and proves accountability.
5. Review Encryption Standards
- For communicating data, only TLS 1.2 or higher shall be used, and for storing it, AES-256 encryption will be applied, along with secure key management practices.
- Check whether the encryption on mobile devices allows secure access to the fields. These standards avoid data interception, maintaining the integrity of the investigation.
6. Evaluate Vendor CJIS Expertise
- Examine the vendor’s longevity and service to law enforcement over the decades to validate the reliability of the signal.
- Verify the presence of devoted CJIS experts who are helping in the preparation of audits.
- Request for records and customer references to prove successful CJIS audits.
7. Understand Total Cost of Compliance
- Calculate initial setup, continual maintenance, upgrades, and audit assistance costs.
- Reveal concealed costs such as hardware or IT staff time. Transparent pricing shows a true dedication to long-term compliance.
8. Assess Long-Term Compliance Maintenance
- Identify how vendors update the CJIS policy tracking and take responsibility for adaptations.
- Discuss agency liabilities in case of a change in requirements. Proactive vendors protect the business from possible interruptions in the future.
PsPortal and similar solutions are good examples of these criteria because of their purpose-built architecture, 30+ years of law enforcement experience, and complete compliance assistance, but agencies always confirm the claims with documents and references.
Start using this framework right away to choose software that meets the CJIS requirements and improves the performance of the agency.
Common CJIS Compliance Mistakes Police Departments Must Avoid
Understanding CJIS requirements for law enforcement is done through recognizing the points at which agencies usually make mistakes. Such errors pose a threat to database access and operations, but can be avoided by simply having the proper awareness and planning.
1. Assuming “Cloud” Automatically Means Compliant
- Cloud providers will be required to sign Security Addendums and accept the mandatory CJIS standards for police purposes.
- Check particular CJIS compliance documentation, not only general security certificates. Generic cloud services do not satisfy the federal requirements.
2. Overlooking Third-Party Vendor Access
- All transcription services, IT contractors, and backup providers are required to comply with CJIS.
- Vendors involved with CJI will have to sign the Security Addendums, and there will be no exceptions for “indirect” access.
3. Incomplete Background Checks
- The law at the federal level necessitates the use of fingerprint-based FBI background checks for every person who has direct access to CJI.
- Only state checks are not sufficient to fulfill the requirements. This covers everyone, including contractors and civilian staff, and not merely sworn officers.
4. Inadequate Audit Logging
- Access logs alone will not be sufficient; the CJIS standard necessitates logging of all queries along with a minimum one-year retention period.
- Multiple systems may record logins, but may not have the detailed audit trails that federal auditors require.
5. Treating Compliance as a One-Time Project
- Continuous attention is a fundamental requirement of CJIS compliance.
- Changes in policy, personnel replacements, and new technology result in unending responsibilities.
- Yearly training and periodic audits are operational requirements that cannot be avoided; they are simply mandatory.
6. Failing to Secure Mobile Devices
- Patrol devices (laptop, tablet, and smartphone) accessing CJI must fulfill overall CJIS specifications.
- Remote wipe capability, encryption, and multi-factor authentication apply to all mobile access points.
7. Not Preparing for CJIS Audits
- Agencies go into agitation when audits come instead of keeping audit-ready documentation. Arrange policies, procedures, and audit logs neatly and make them available instantly.
8. Selecting Software Based on Price Alone
- Non-compliant services lead to substantial financial losses when access to the database is cut off. Evaluate mandatory CJIS standards for police, then go to features and pricing. Compliance is not negotiable.
These mistakes have a common link: they can be easily avoided through proper planning and checking of vendors. Agencies that consider these weaknesses now are able to protect their database access and operational readiness before the audits arrive.
Budget Justification: Why CJIS-Compliant Software is a Mission-Critical Investment
Establishing CJIS-compliant software as non-negotiable infrastructure that powers every operation is one way police departments secure funding and, at the same time, highlight why CJIS compliance is mandatory. Access to databases is a necessary tool for performing police functions, including patrol, investigation, dispatch, and records management.
Non-compliant software does not bring about minor inconveniences; instead, it leads to the total shutdown of operations.
Mission-Critical Infrastructure:
- CJIS-compliant systems are considered indispensable along with patrol cars, radios, and guns as the basic requirements for police operations.
- The budget authorities readily approve these items, as the police force will stop if they are not available.
- Database access deserves the same status; the officers cannot function without access to NCIC, NLETS, and state systems.
Risk Mitigation ROI
- Compliance costs considerably less than the penalties of non-compliance.
- Database access loss results in a stoppage of investigations, a risk to officer safety, and prevents warrant verification.
- Data leakage incidents due to non-compliant systems cost up to millions in terms of remediation, legal penalties, and liability exposure.
- CJIS compliance importance is indisputable when software investment is compared to the cost of one week without NCIC access.
Operational Efficiency Gains
- The specialized purpose-built compliance systems have resulted in faster response to queries, lighter IT load, and better prepared audits.
- Converted into resolved cases, secured officers, and time saved for administration, as well as measurable operational value, which is even greater than DIY compliance.
Financial Advantages
- Compliance with CJIS permits access to grants from both the federal and state governments. In addition, many funding programs have compliance as a prerequisite for receiving the money.
- Portal XL and other similar cloud-based solutions do not require a local infrastructure that is costly, hardware that is constantly being updated, and IT personnel who are dedicated to the system.
- Changes in compliance managed by the vendor cost less than the management of compliance by internal management.
Budget Comparison Framework
- Perform a cost comparison between the compliant software investment and the operational costs during a database access suspension.
- Within just one week of going without access to NCIC, the financial case becomes apparent that compliance is not at all expensive, while non-compliance is unfortunate.
The Business Case: The price of regulatory software is trivial in comparison to the cost of a week’s database access loss. Police forces cannot work anymore as their operations are completely shut down. This is not a metaphor; it’s the reality of the operation. Compliance is not optional; it’s a necessary investment in infrastructure.
Frequently Asked Questions About Mandatory CJIS Compliance
Why is CJIS compliance mandatory for all police software?
CJIS compliance is a must since federal statutes command the safeguarding of CJI, which is made available via systems like NCIC. The reason for making CJIS compliance mandatory originates from the 28 U.S.C. § 534 law, which obligates the secure management of national crime databases.
What happens if our police department uses non-CJIS-compliant software?
The non-compliant software causes an instant NCIC database lockout, stopping operations related to investigations, warrants, and officer safety checks, resulting in complete disruption until the issue is fixed.
How do we verify a police software vendor is truly CJIS compliant?
Ask for the signed CJIS Security Addendum, examine their FBI authorization letter, and compare their policy documents with police-mandatory CJIS standards. Do vendor reviews every three months.
What is the best CJIS compliance solution for police departments?
PsPortal provides the most reliable CJIS compliance solution for police, as it has a secure database access infrastructure layer designed explicitly for the PsPortal CJIS obligatory compliance software, meeting the law enforcement software CJIS requirements without reconstruction.
Does CJIS compliance apply to cloud-based police software?
Yes, it is necessary for cloud service providers to execute the Security Addendum and comply with all controls and check the FBI’s authorization since standard cloud security is not adequate.
How much does CJIS-compliant police software cost?
Different agencies have different prices, and the typical range is from $5K to $50 per year. Still, compliant systems provide ROI by preventing downtime and reducing remediation costs, which are more than $500K per breach.
How often do police departments get audited for CJIS compliance?
Federal audits happen every 3 to 5 years. Moreover, state or local examinations and inspections that are initiated keep the facility in an audit-ready status by performing self-assessments yearly.
Mandatory CJIS Compliance: Foundation for Modern, Secure Law Enforcement
Why CJIS compliance is mandatory isn’t a complicated question. Federal law makes it a must. The FBI allows access to the national crime databases with the condition that the agencies safeguard that information by implementing extensive security controls. Those security controls are CJIS standards.
The consequences are very serious. Defying the rules leads to instant termination of database access, no delay, no gradual process, just immediate termination. Law enforcement activities become impossible, the safety of police personnel is compromised, and the quality of service to the public is reduced.
Purpose-built solutions matter. The use of general-purpose software with retrofitted CJIS compliance features leads to constant risks and management challenges. Law enforcement requirements-based solutions, such as CJIS-compliant police software PsPortal, simplify compliance and lower the risk.
Compliance is an investment in operational capability rather than only a regulatory obligation. A safe and reachable database infrastructure allows the police to be effective and accountable. Police work more safely. The detectives are quicker in their work. The people are served better.
There is no need to wait for the auditing time or the termination of the database access to assess the compliance. Carry out an audit today, check the compliance of the vendor, and choose the solutions that are specifically made for your requirements.
Get in touch with PsPortals right away. Infrastructure built for compliance from the very beginning is what your operations and your staff deserve.